|
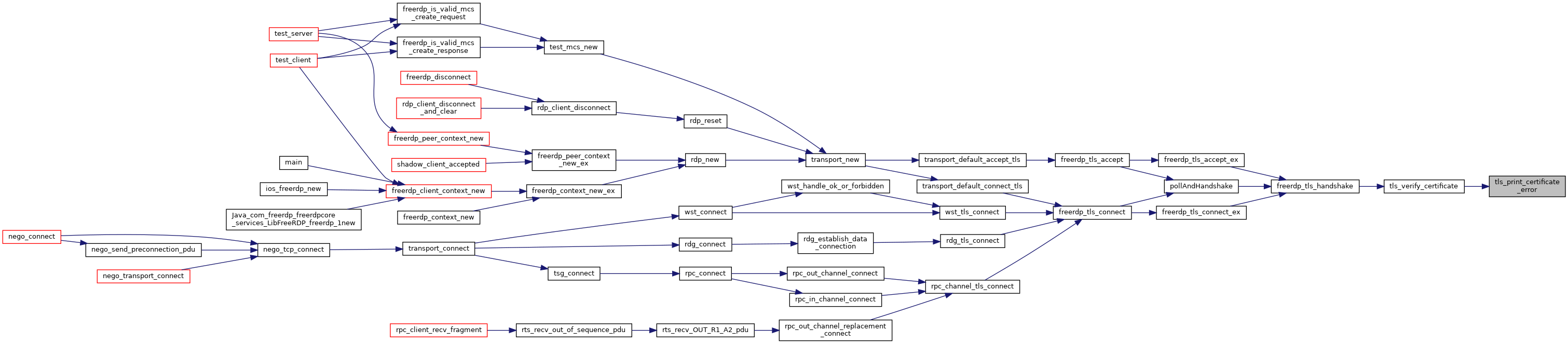
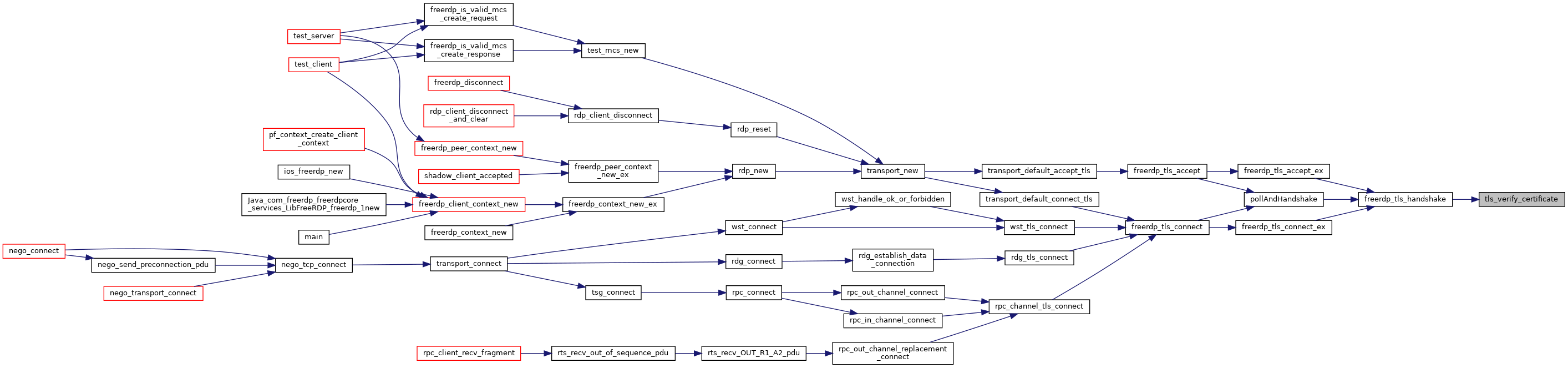
| static int | tls_verify_certificate (rdpTls *tls, const rdpCertificate *cert, const char *hostname, UINT16 port) |
| |
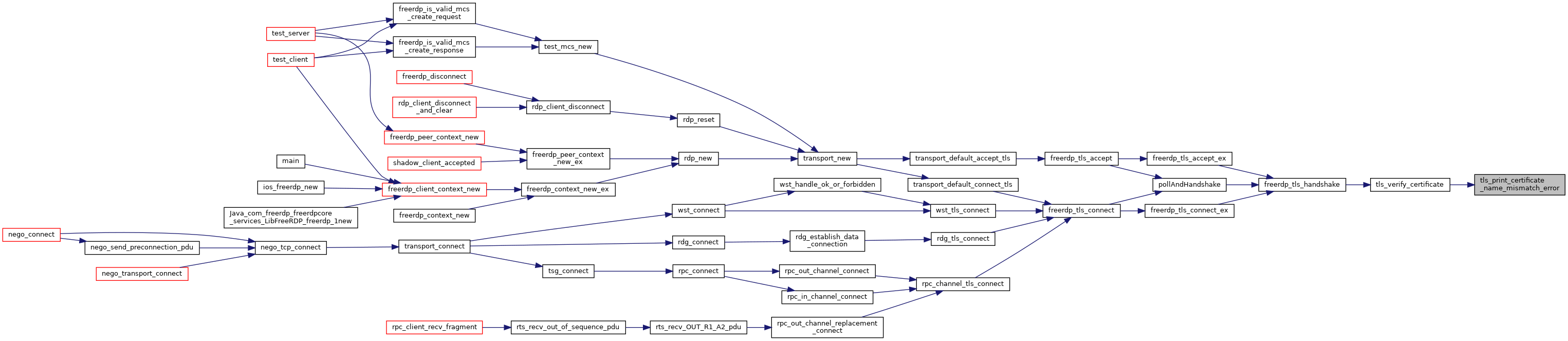
| static void | tls_print_certificate_name_mismatch_error (const char *hostname, UINT16 port, const char *common_name, char **alt_names, size_t alt_names_count) |
| |
| static void | tls_print_new_certificate_warn (rdpCertificateStore *store, const char *hostname, UINT16 port, const char *fingerprint) |
| |
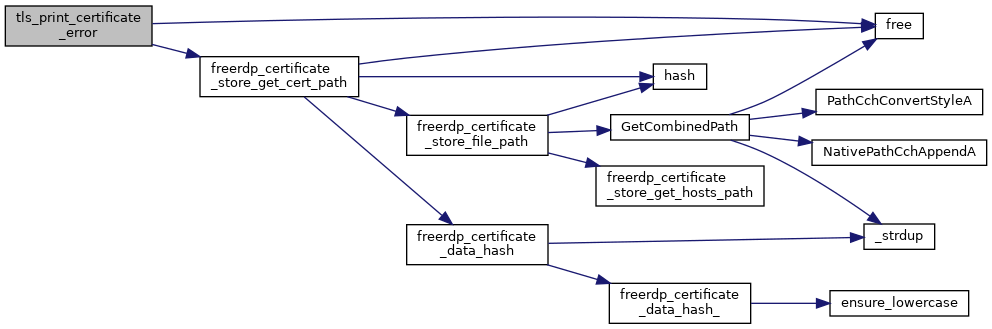
| static void | tls_print_certificate_error (rdpCertificateStore *store, rdpCertificateData *stored_data, const char *hostname, UINT16 port, const char *fingerprint) |
| |
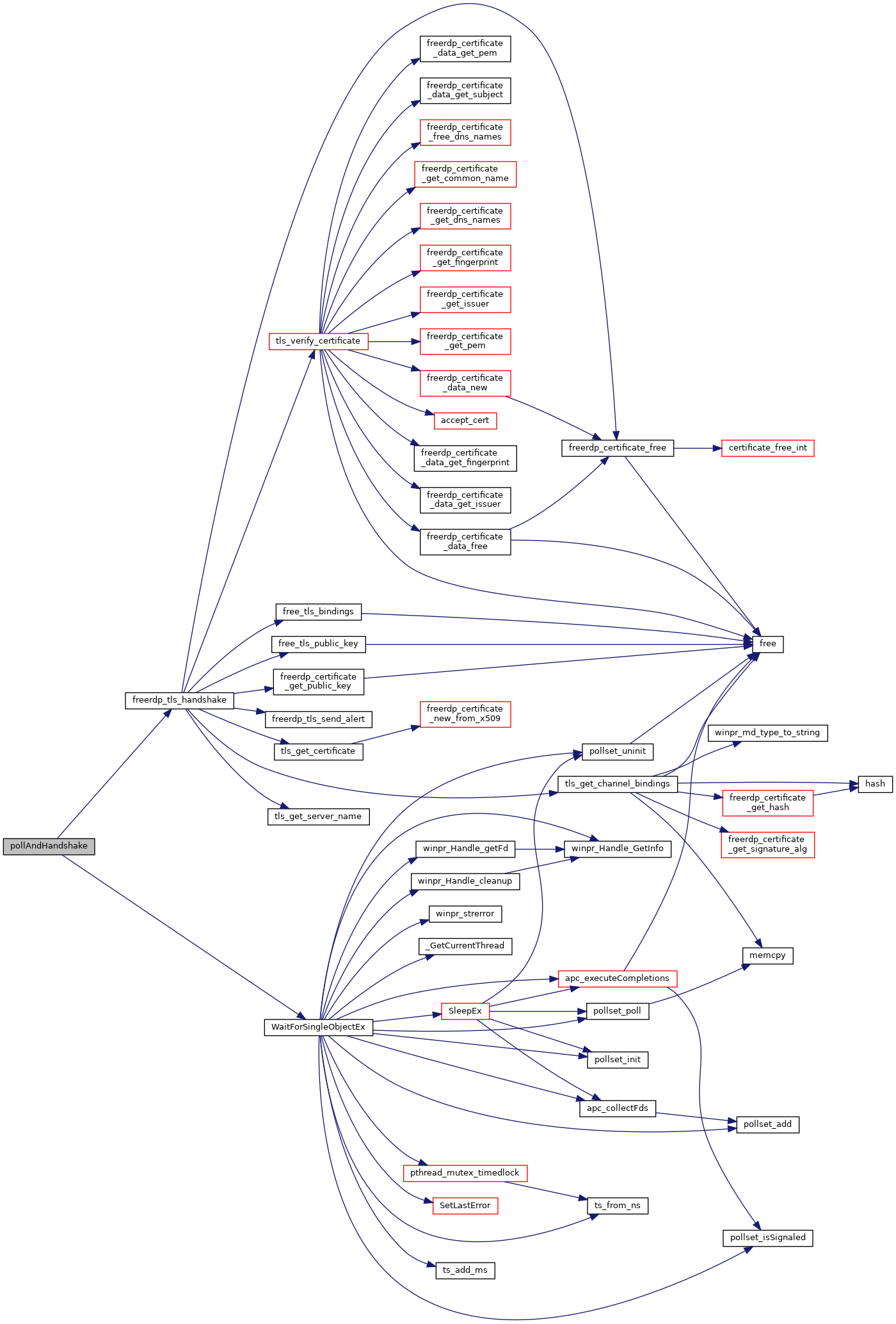
| static void | free_tls_public_key (rdpTls *tls) |
| |
| static void | free_tls_bindings (rdpTls *tls) |
| |
| static int | bio_rdp_tls_write (BIO *bio, const char *buf, int size) |
| |
| static int | bio_rdp_tls_read (BIO *bio, char *buf, int size) |
| |
| static int | bio_rdp_tls_puts (BIO *bio, const char *str) |
| |
| static int | bio_rdp_tls_gets (BIO *bio, char *str, int size) |
| |
| static long | bio_rdp_tls_ctrl (BIO *bio, int cmd, long num, void *ptr) |
| |
| static int | bio_rdp_tls_new (BIO *bio) |
| |
| static int | bio_rdp_tls_free (BIO *bio) |
| |
| static long | bio_rdp_tls_callback_ctrl (BIO *bio, int cmd, bio_info_cb *fp) |
| |
| static BIO_METHOD * | BIO_s_rdp_tls (void) |
| |
| static BIO * | BIO_new_rdp_tls (SSL_CTX *ctx, int client) |
| |
| static rdpCertificate * | tls_get_certificate (rdpTls *tls, BOOL peer) |
| |
| static const char * | tls_get_server_name (rdpTls *tls) |
| |
| static SecPkgContext_Bindings * | tls_get_channel_bindings (const rdpCertificate *cert) |
| |
| static BOOL CALLBACK | secrets_file_init_cb (PINIT_ONCE once, PVOID param, PVOID *context) |
| |
| static void | SSLCTX_keylog_cb (const SSL *ssl, const char *line) |
| |
| static void | tls_reset (rdpTls *tls) |
| |
| static BOOL | tls_prepare (rdpTls *tls, BIO *underlying, SSL_METHOD *method, int options, BOOL clientMode) |
| |
| static void | adjustSslOptions (int *options) |
| |
| const SSL_METHOD * | freerdp_tls_get_ssl_method (BOOL isDtls, BOOL isClient) |
| |
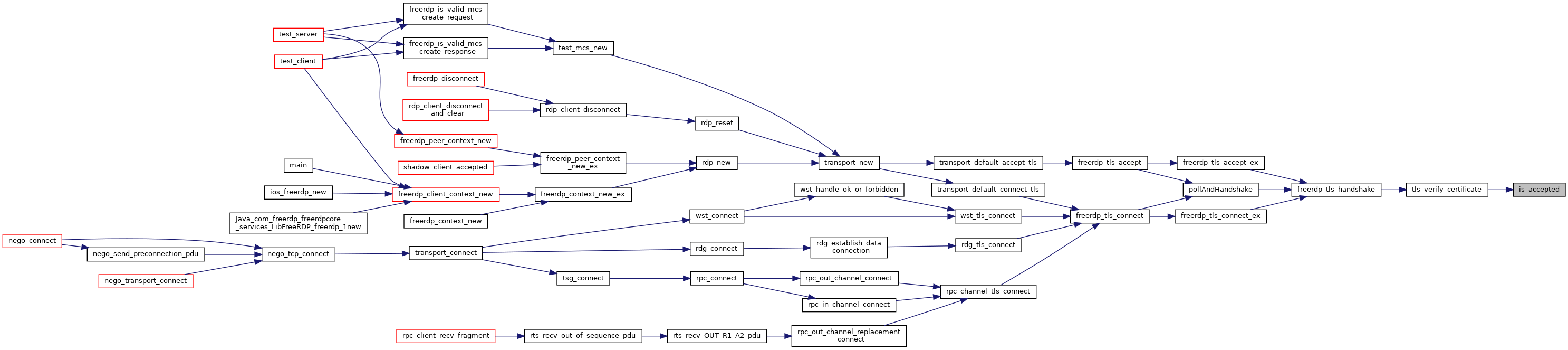
| TlsHandshakeResult | freerdp_tls_connect_ex (rdpTls *tls, BIO *underlying, const SSL_METHOD *methods) |
| |
| static int | bio_err_print (const char *str, size_t len, void *u) |
| |
| TlsHandshakeResult | freerdp_tls_handshake (rdpTls *tls) |
| |
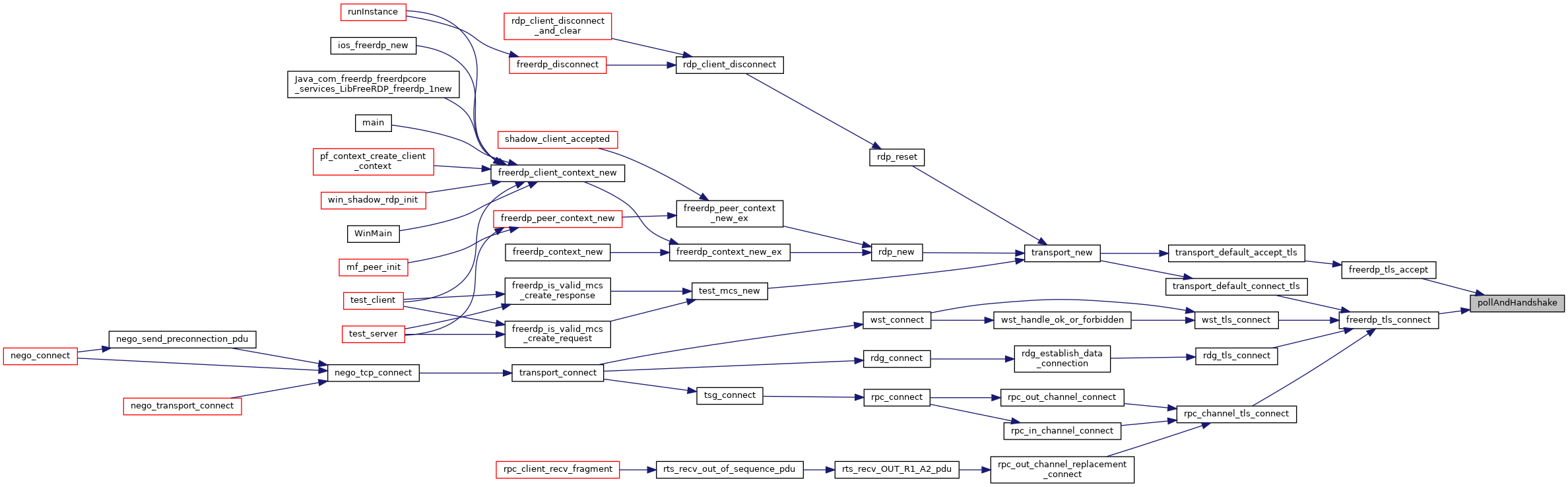
| static int | pollAndHandshake (rdpTls *tls) |
| |
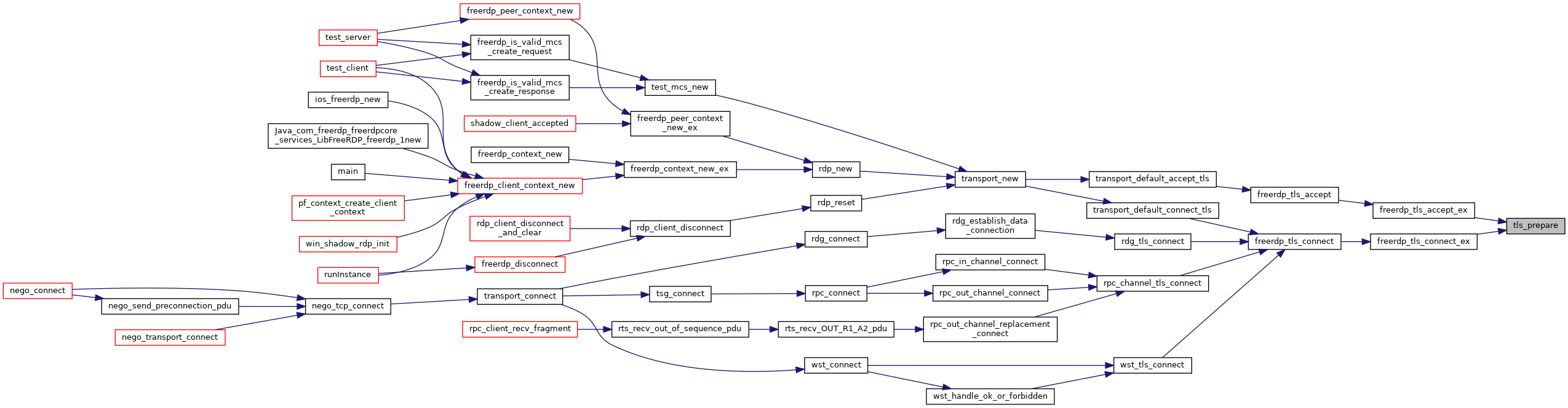
| int | freerdp_tls_connect (rdpTls *tls, BIO *underlying) |
| |
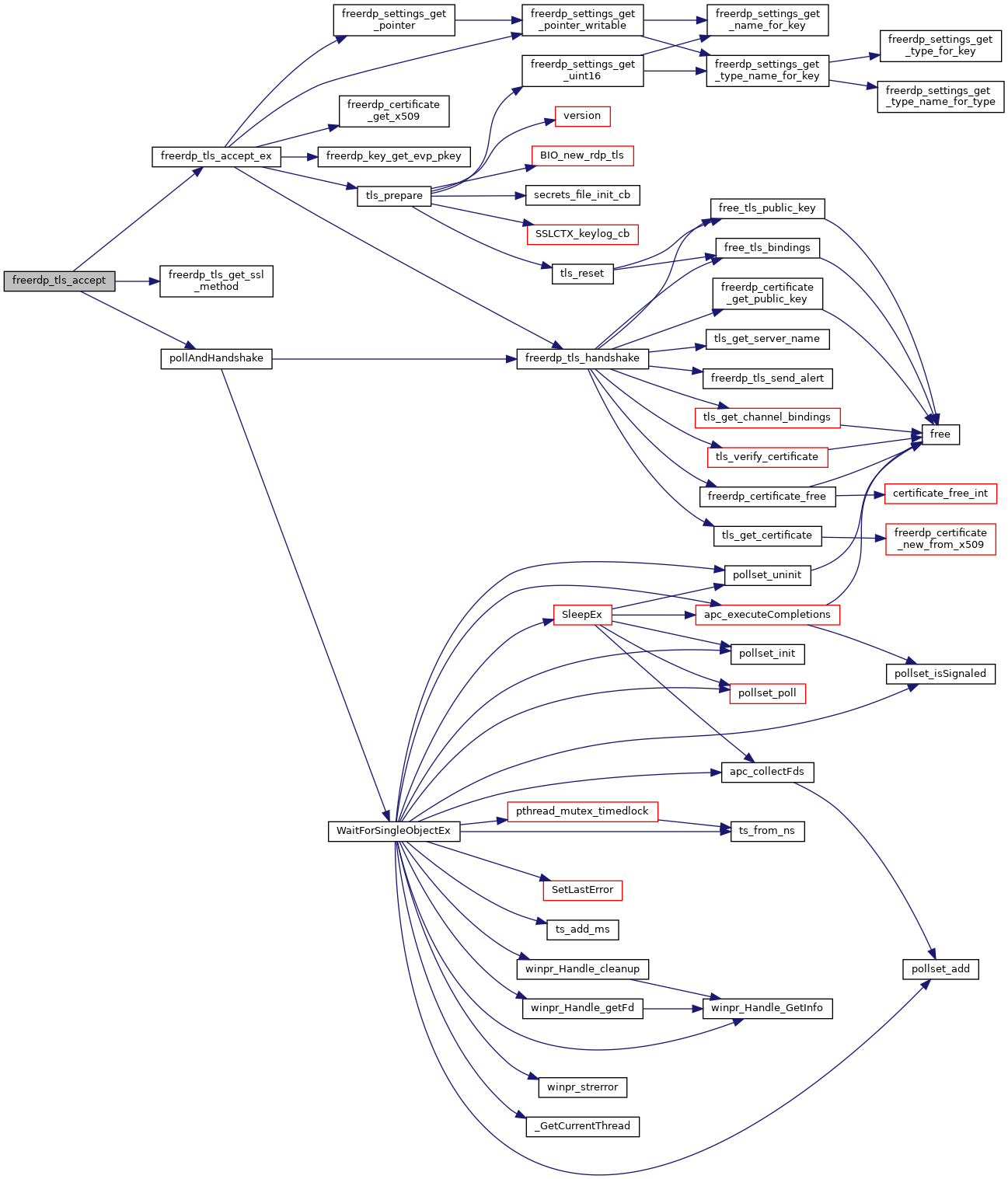
| BOOL | freerdp_tls_accept (rdpTls *tls, BIO *underlying, rdpSettings *settings) |
| |
| TlsHandshakeResult | freerdp_tls_accept_ex (rdpTls *tls, BIO *underlying, rdpSettings *settings, const SSL_METHOD *methods) |
| |
| BOOL | freerdp_tls_send_alert (rdpTls *tls) |
| |
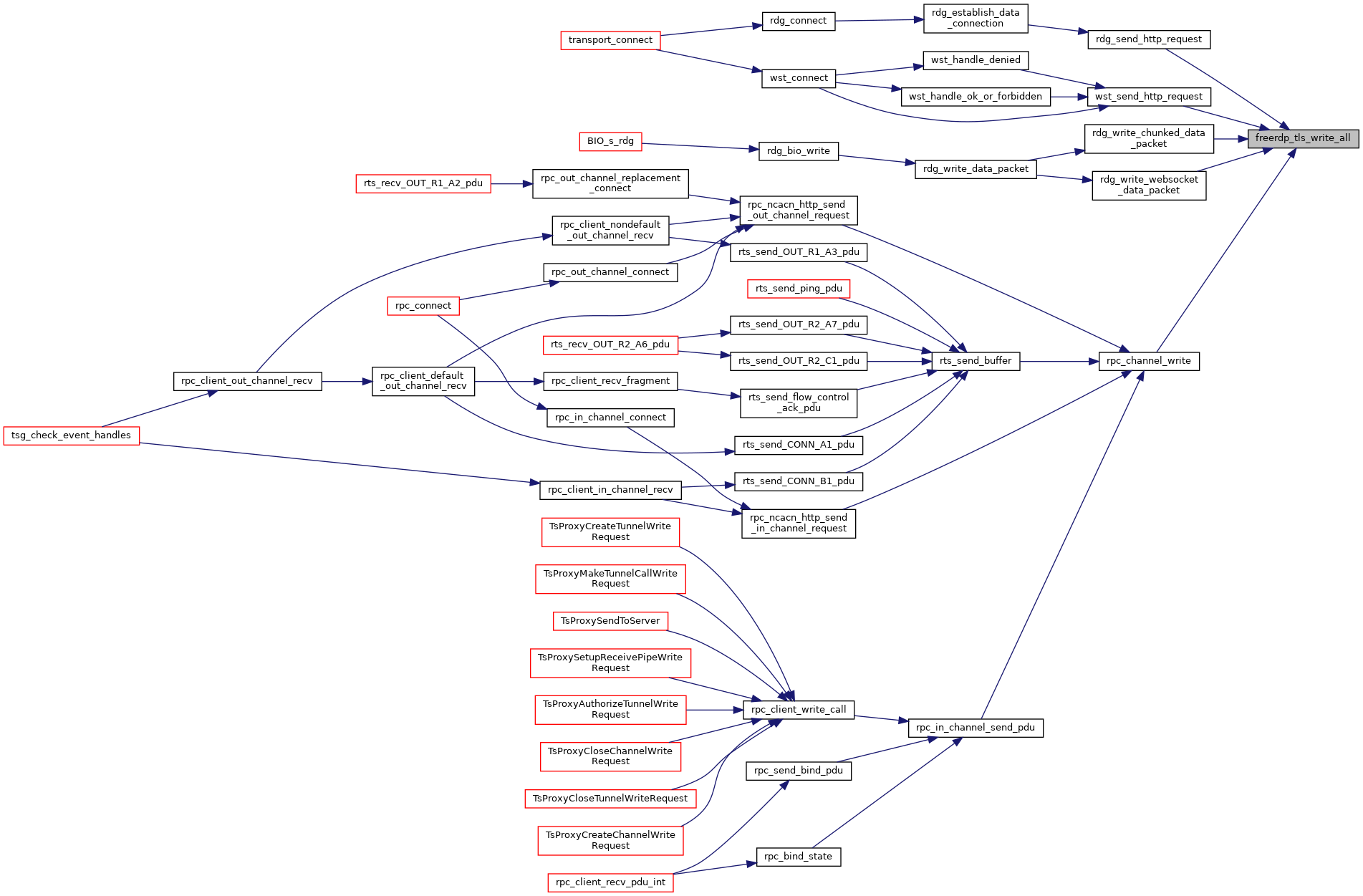
| int | freerdp_tls_write_all (rdpTls *tls, const BYTE *data, int length) |
| |
| int | freerdp_tls_set_alert_code (rdpTls *tls, int level, int description) |
| |
| static BOOL | tls_match_hostname (const char *pattern, const size_t pattern_length, const char *hostname) |
| |
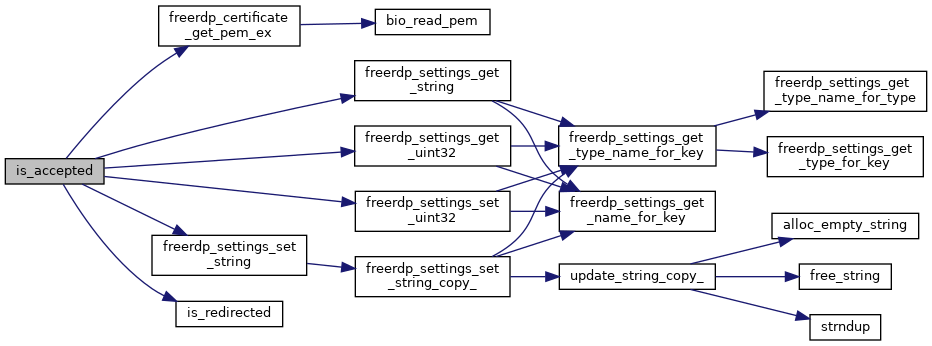
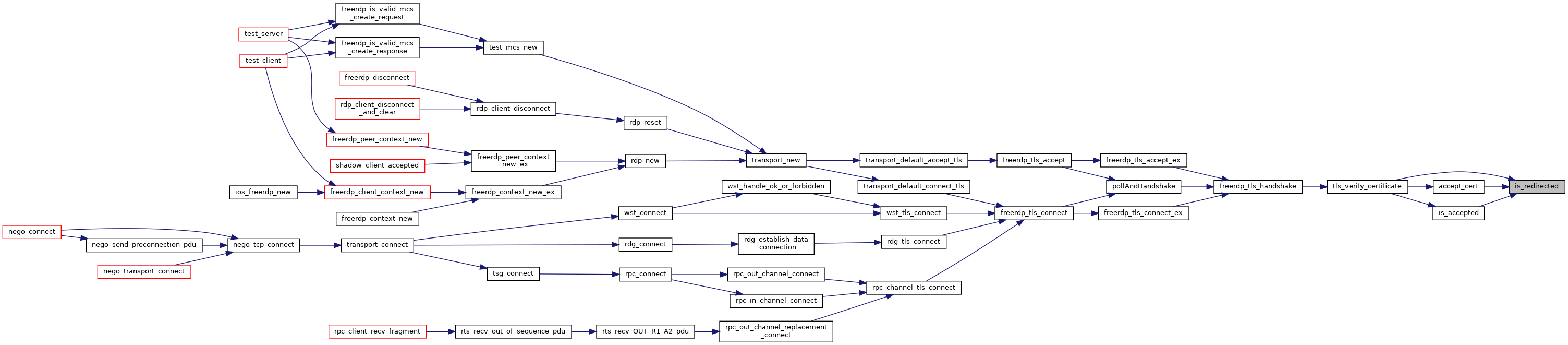
| static BOOL | is_redirected (rdpTls *tls) |
| |
| static BOOL | is_accepted (rdpTls *tls, const rdpCertificate *cert) |
| |
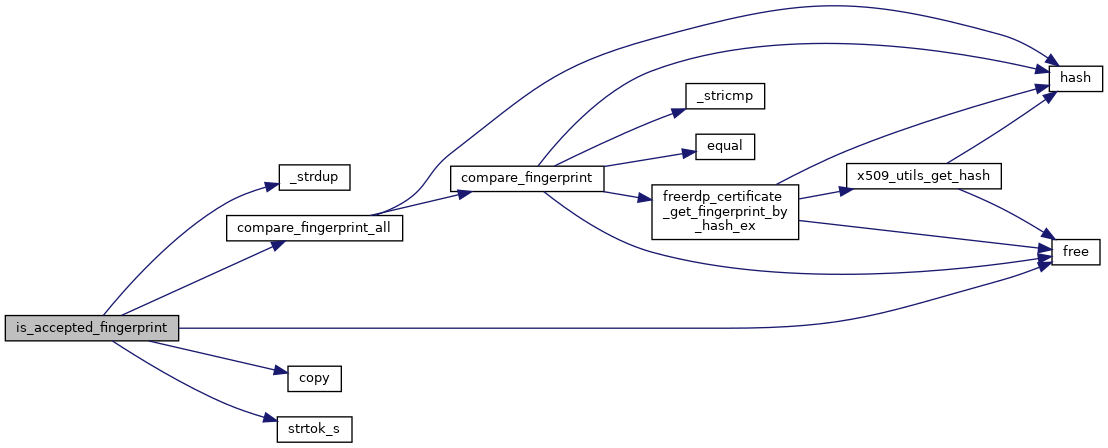
| static BOOL | compare_fingerprint (const char *fp, const char *hash, const rdpCertificate *cert, BOOL separator) |
| |
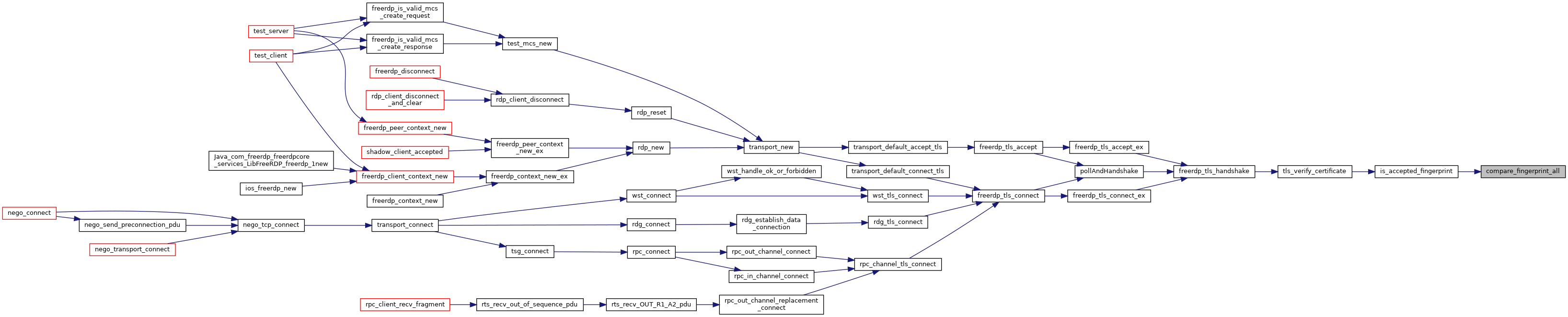
| static BOOL | compare_fingerprint_all (const char *fp, const char *hash, const rdpCertificate *cert) |
| |
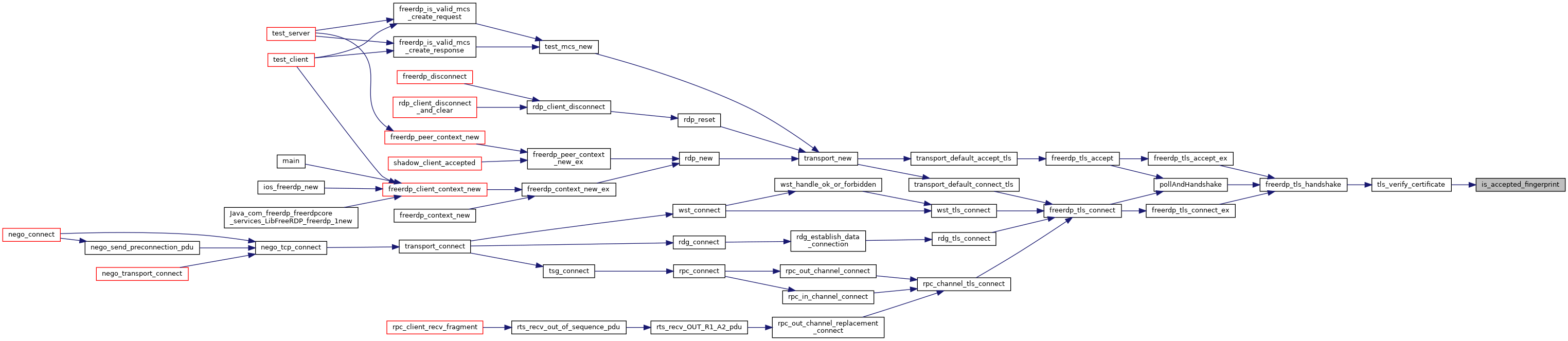
| static BOOL | is_accepted_fingerprint (const rdpCertificate *cert, const char *CertificateAcceptedFingerprints) |
| |
| static BOOL | accept_cert (rdpTls *tls, const rdpCertificate *cert) |
| |
| static BOOL | tls_extract_full_pem (const rdpCertificate *cert, BYTE **PublicKey, size_t *PublicKeyLength) |
| |
| rdpTls * | freerdp_tls_new (rdpContext *context) |
| |
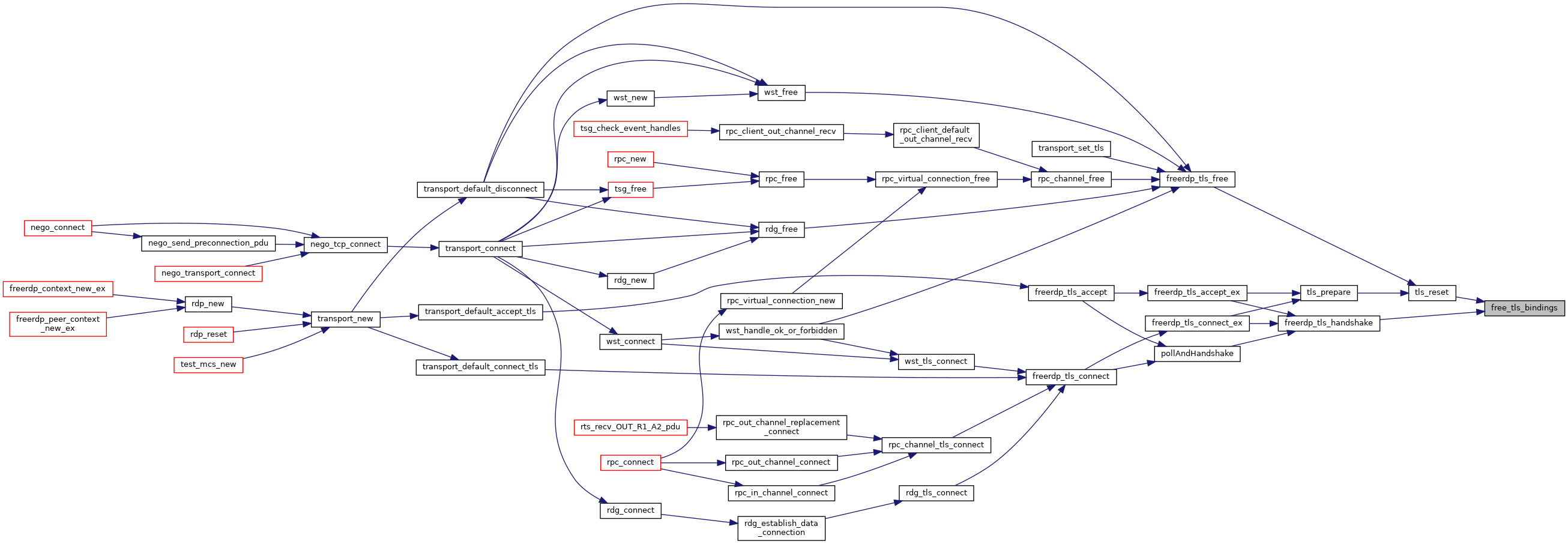
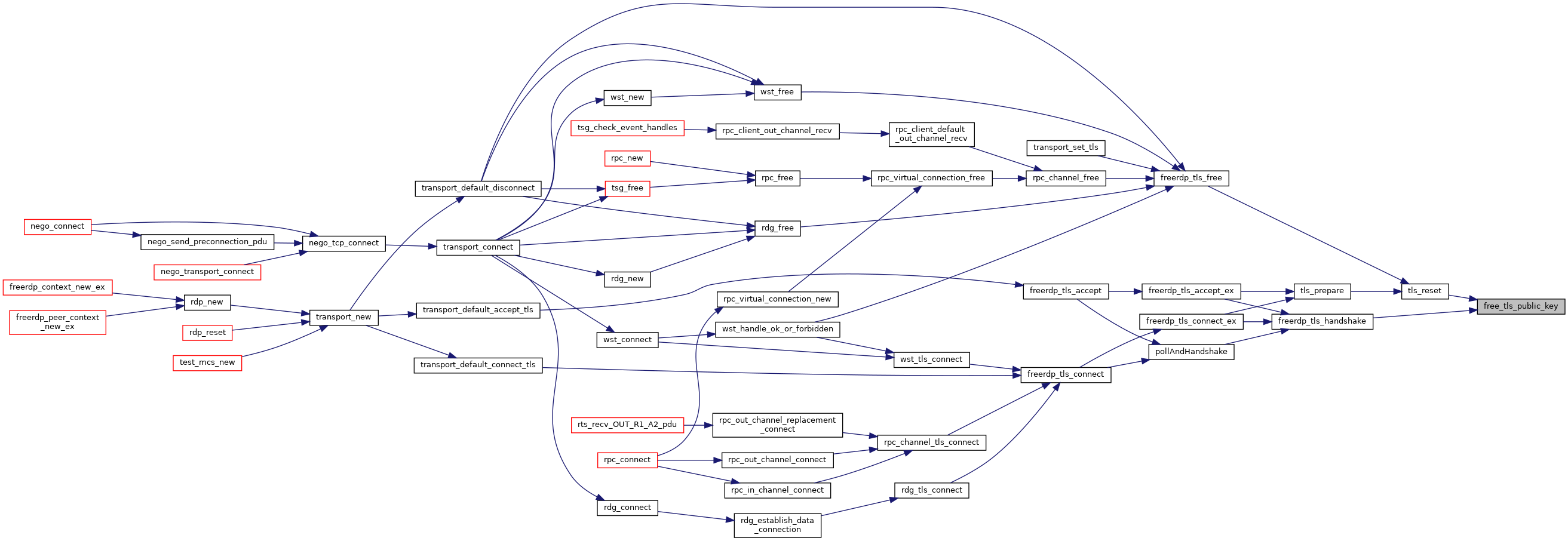
| void | freerdp_tls_free (rdpTls *tls) |
| |
FreeRDP: A Remote Desktop Protocol Implementation Transport Layer Security
Copyright 2011-2012 Marc-Andre Moreau marca.nosp@m.ndre.nosp@m..more.nosp@m.au@g.nosp@m.mail..nosp@m.com Copyright 2023 Armin Novak anova.nosp@m.k@th.nosp@m.incas.nosp@m.t.co.nosp@m.m Copyright 2023 Thincast Technologies GmbH
Licensed under the Apache License, Version 2.0 (the "License"); you may not use this file except in compliance with the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software distributed under the License is distributed on an "AS IS" BASIS, WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied. See the License for the specific language governing permissions and limitations under the License.
| TlsHandshakeResult freerdp_tls_accept_ex |
( |
rdpTls * |
tls, |
|
|
BIO * |
underlying, |
|
|
rdpSettings * |
settings, |
|
|
const SSL_METHOD * |
methods |
|
) |
| |
SSL_OP_NO_SSLv2:
We only want SSLv3 and TLSv1, so disable SSLv2. SSLv3 is used by, eg. Microsoft RDC for Mac OS X.
SSL_OP_NO_COMPRESSION:
The Microsoft RDP server does not advertise support for TLS compression, but alternative servers may support it. This was observed between early versions of the FreeRDP server and the FreeRDP client, and caused major performance issues, which is why we're disabling it.
SSL_OP_TLS_BLOCK_PADDING_BUG:
The Microsoft RDP server does not support TLS padding. It absolutely needs to be disabled otherwise it won't work.
SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS:
Just like TLS padding, the Microsoft RDP server does not support empty fragments. This needs to be disabled.
SSL_OP_NO_RENEGOTIATION
Disable SSL client site renegotiation.
| TlsHandshakeResult freerdp_tls_connect_ex |
( |
rdpTls * |
tls, |
|
|
BIO * |
underlying, |
|
|
const SSL_METHOD * |
methods |
|
) |
| |
SSL_OP_NO_COMPRESSION:
The Microsoft RDP server does not advertise support for TLS compression, but alternative servers may support it. This was observed between early versions of the FreeRDP server and the FreeRDP client, and caused major performance issues, which is why we're disabling it.
SSL_OP_TLS_BLOCK_PADDING_BUG:
The Microsoft RDP server does not support TLS padding. It absolutely needs to be disabled otherwise it won't work.
SSL_OP_DONT_INSERT_EMPTY_FRAGMENTS:
Just like TLS padding, the Microsoft RDP server does not support empty fragments. This needs to be disabled.